July 10, 2024
10 Min Read

In this post we will focus on how we can align our cyber resilience goals to real-world threats and implement a strategy to adapt to multiple failure points if our endpoint defenses are impaired during an attack. For this example, we will start by applying some key principals of NIST Special Publication (SP) 800-160, Volume 2 in conjunction with the MITRE ATT&CK Framework to understand the attack path an adversary would take to disrupt or disable endpoint detection and prevention controls. Then we’ll develop a resilience strategy that will enable us to withstand and recover from this type of attack.
Before we begin, we first need to accept that no matter how well prepared we are, there is aways the potential that an adversary is going to out-maneuver our detections and defenses. This is regardless of how well our security staff is trained, the thoroughness of our processes, and the capabilities of the technologies we have implemented.
Secondly, we need to accept that attackers can maintain persistence in our environments for extended periods of time before they are detected. This could mean detection times spanning weeks, months, or even years following a compromise. For example, software supply-chain are known to have long dwell times. A notable example is the SUNBURST SolarWinds Orion incident (CVE-2020-10148) in 2020 that took over 100 days to detect after initial access to the victim’s environment. In the worst cases, an intrusion may never be detected, so many of the cyber resiliency techniques and approaches that we consider and implement should make this assumption.
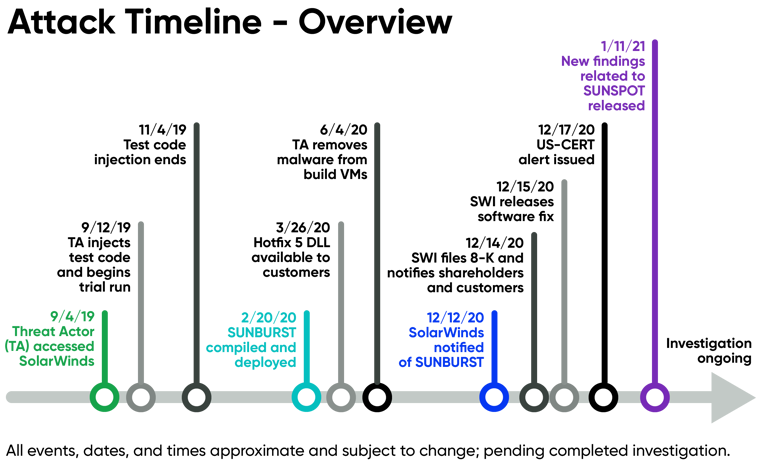
Reference: New Findings From Our Investigation of SUNBURST
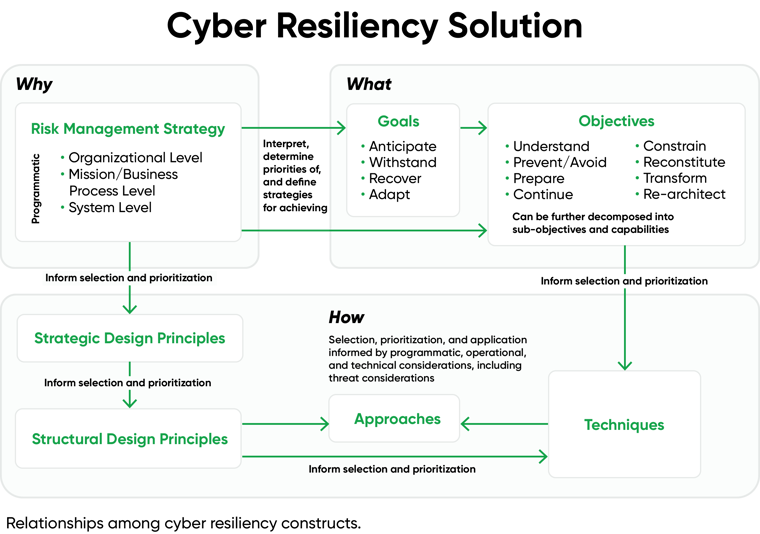
Now that we have accepted that no single solution is fool proof, the next step is to develop a flexible strategy that meets the four high level goals of cyber resiliency, which is the ability to anticipate, withstand, recover from, and adapt to adversity. Adversity in this context is any stealthy, persistent, sophisticated, and well-resourced adversary (i.e., the APT) who may have compromised system components and established a foothold within an organization’s systems.
Once our goals and objectives are defined so that we understand what capabilities are needed or the “what” of our cyber resilience solution, we can then move onto the “how”. These are the techniques and implementation approaches that we can use to achieve the four resilience goals defined below and discussed in the next section.
Per the MITRE web site, the “MITRE ATT&CK® is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.”
In this exercise we are going to use the MITRE ATT&CK framework to understand the TTPs (tactics, techniques, and procedures) that an adversary would use to evade our endpoint defenses and then map those to our four resilience goals. This starts with understanding the attack life cycle, which generally flows from left to right using various tactics to achieve a specific goal. Following reconnaissance of a victim, an adversary will commonly gain initial access through a targeted phishing attack, stolen credentials, and follow an attack path incorporating various other TTPs to reach their final objective such as exfiltrating data and deploying post-exfiltration ransomware.
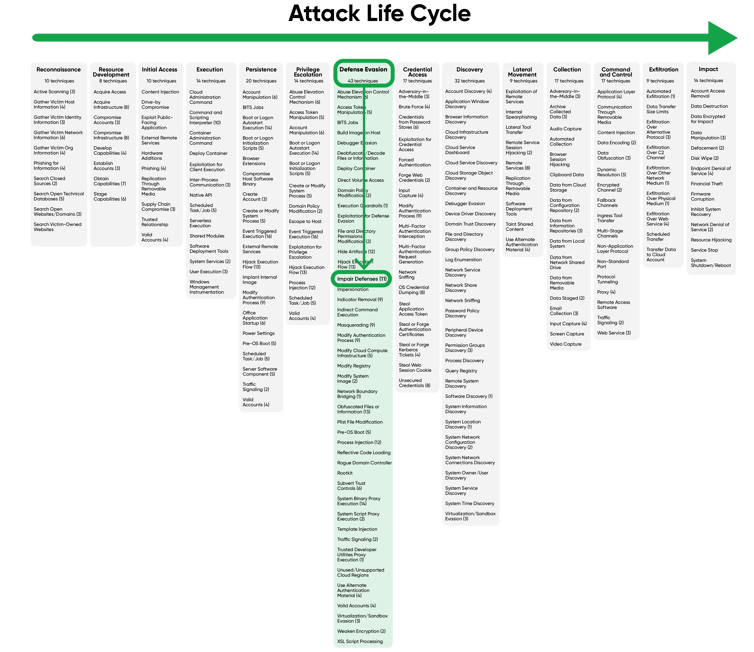
Looking at the tactics from left to right, we can understand the reason an adversary is performing an action for each phase of the attack lifecycle. The tactic "Defense Evasion" is what an adversary would be looking to accomplish once they have been able advance further right in the attack lifecycle during or after initial access attempts but are unwilling or unable to reach the next phase of the attack. This could be due to concern over creating events that might indicate their presence in the environment or an EDR tool that is prohibiting the adversary from proceeding. The techniques in the attack path describe how the adversary intends to achieve the tactic. In this case, the desired outcome is to impair the defenses of the victim by using one of many sub-techniques to disable or modify tools.
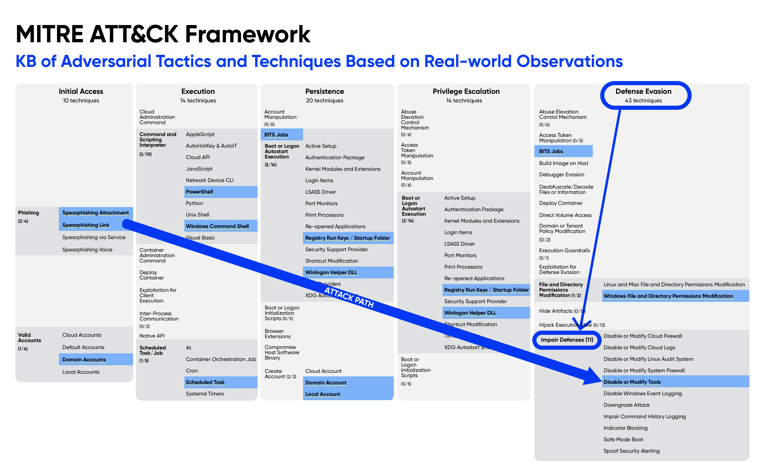
Now we have arrived at our first goal of cyber resilience, which is anticipating that an adversary will attempt to impair our defenses. We need to prepare for these types of attacks and can do that by researching methods of performing these sub-techniques for this anticipated attack vector. Some of the techniques that have been used successfully in the past to bypass endpoint defenses are listed below.
After anticipating everything that an attacker may do to circumvent our endpoint security tools, let us move on to how we can withstand and recover from this attack, meeting two more critical goals of the cyber resilience engineering framework. The first question is how do we detect this type of attack if the adversary has been able to successfully impair our defenses and we never received any alerts from our endpoint tool?
If Absolute Persistence technology is activated, there are many options available to us. Absolute is embedded in over 600 million devices and will survive attempts to disable it, even if the device is re-imaged, the hard drive is replaced, or the firmware is updated. This means we have a leg up on the adversary, since they are generally limited to attacks targeting vulnerabilities in applications or the operating system.
We want to ensure that we are monitoring the health of our installed security applications across the entire fleet and configure alerting for when our endpoint detection and prevention control is experiencing degradation. Next, we want to ensure that our applications are configured for automatic repair and reinstall if an attacker has disabled, corrupted, or uninstalled our endpoint security tool using the Resilience features of Secure Endpoint.
What if repairing or reinstalling is not an option due to a vulnerability in the endpoint security tool for which no known mitigation exists? We might also be in a situation where we have lost supporting infrastructure for our endpoint security tool and even our endpoints due to a compromised privileged account or mass outage caused by ransomware. This presents a very precarious situation where we are not able to regain control of the device, the attacker continues to maintain persistence, we have no way to investigate the impacted endpoint, and our only remaining option is manual intervention with physical access to the device.
With our modern hybrid workforce distributed over many geographic locations this becomes an almost impossible situation to recover from – unless that is we apply the remaining goal of cyber resilience, which is the ability to adapt! With Absolute’s always-on connectivity back to the to the Secure Endpoint console, we can detect, respond, and recover even if the device has been fully compromised. Absolute has the capability to remotely deploy alternative security tools and agents out of band, and if this is not an option, run powerful query and remediation scripts from the Secure Endpoint console.
Now that we understand how to align real-world threats with cyber resilience goals and implement a solution to adapt to multiple failure points, this information should be used to build out our incident response playbook of last resort. This playbook should walk through all the steps required for preparing for an incident where our primary security controls have been disabled and take into consideration that an attack has compromised or disrupted normal capabilities to manage the endpoint fleet. Some key activities to consider might include:
Share this article