June 22, 2022
2 Min Read

An unencrypted enterprise device can place any organization with a well-fortified security strategy at serious risk of being breached. A new report compiled by Absolute found that 16% of endpoints are unencrypted, revealing that this problem is more widespread threat than one might presume. All it takes is one vulnerable lost, stolen, or compromised endpoint to cause an incident.
16% of enterprise devices are unencrypted.
*Data pulled from >4.2M Absolute-enabled active enterprise devices.
If an unencrypted device is connected to a corporate network in an office setting, the risk of a breach is reduced. In the world of remote work however, if an enterprise device remains unencrypted it means that any communications sent to or from it can pose a security risk, especially when connected to a network outside of the office.
Day-to-day, remote employees are using enterprise devices in on numerous networks and in multiple locations. In fact, the latest data from Absolute shows that on average, enterprise devices are being used in four different locations per day.
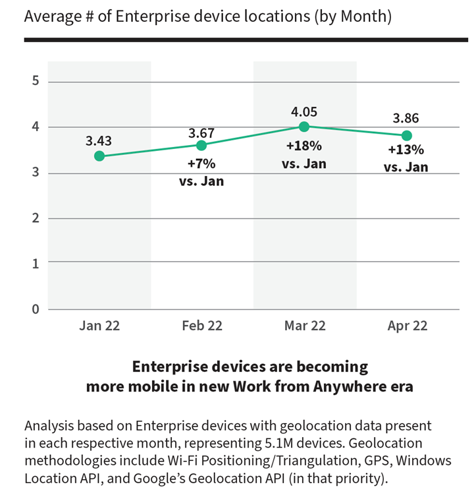
In today’s work from anywhere world, unencrypted devices become inviting targets for bad actors looking for a weak link to exploit.
Unhealthy encryption is not rare
In the event of a breach, enterprise devices contain sensitive data that could result in costly financial and reputational damage to an organization. Absolute’s recent Endpoint Risk Report found that 22% of devices reported unhealthy encryption controls, providing further proof that organizations have struggled to maintain encryption for their employee’s machines.
The chance of a malicious third-party accessing sensitive corporate data, applications, or networks through a vulnerable endpoint is an ever-present reality for organizations with mobile workers scattered around the globe.
In response companies need to have a comprehensive security strategy that validates user identities regardless of where they may be in the world. And a Zero Trust security solution is ideal to help mitigate the risks of an unencrypted company device.
A Zero Trust solution helps combat unencrypted devices
The multifaceted approach of a Zero Trust security strategy places several important tools in IT’s hands. By redefining the network ‘perimeter,’ IT teams are empowered to set their own requirements for contextual identity verification that protects an entire dispersed workforce. This ensures that IT can verify every employees network connection.
Additionally, being able to see if encryption is faltering is crucial for IT. The degradation of encryption leaves enterprise devices vulnerable to breaches. This highlights the growing need for endpoint visibility so that IT can address security issues as they arise as well as remediate compromised security applications on remote mobile phones and laptops.
Organizations that focus on visibility and control to their enterprise devices stand the best chance of identifying and eliminating unencrypted devices. This is one reason that companies are rapidly turning their sights towards a Zero Trust approach to protect employees and their data.
Adopting a reliable, self-healing zero trust solution provides security professionals the peace of mind that they require in today’s remote working world.
Adopting your own Zero Trust strategy
If your organization is looking to find a better way to implement a Zero Trust strategy or to learn more about the increased risks faced by hybrid and mobile workforces, read Absolute’s new report “The value of Zero Trust in a WFA world”. You can also reach out to book a demo with Absolute now.
Share this article